If we are using the Dynamics 365 in an Enterprise Level , System Integrations with Web APIs are a common scenario. This post will explain on how to set up Azure Active Directory Authentication on Web APIs
1. Register the Web API application in Azure Active directory , To do that Navigate to Azure Portal and Click on 'Azure Active Directory' -> 'App Registrations' -> 'New Application registration'
2. Provide any relevant name and 'Sign On Url' as your Web API Url postfixed by ".auth/login/aad/callback"
then click on create.
Ex: - http://<<your webapi Url >>/.auth/login/aad/callback , http://xxxxxx.azurewebsites.net/.auth/login/aad/callback
3. Once created , The Application Id highlighted below will be the 'Client id' that would be used in the next steps.
4. From the Azure Portal - Navigate to your Web API that you have already created. Scroll down and click on 'Authentication/Authorization'
5. Change the 'App Service Authentication' to On , 'Action to take when request is not authenticated' to 'Login with Azure Active directory' and Click on 'Azure Active Directory' Option.
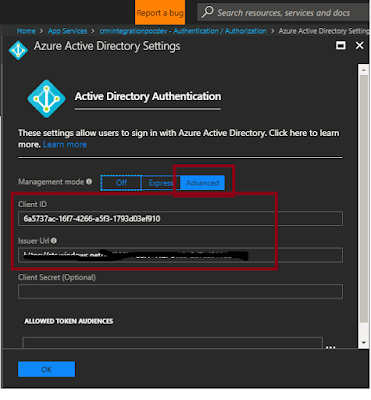
3. In the next screen , Choose the 'Management Mode' as 'Advanced' and Enter the 'ClientId' that is generated from the Step 3 and Issuer Url.
Issuer Url Would be same across all your AAD applications and it would be specific to your Organization ,
Update the field with Issuer URL for your Active Directory postfixed by TenantId of your Active Directory. TenantId can be obtained by executing PowerShell command 'Get-AzureAccount' or by browsing to your directory from the management portal.
Ex:- login.contoso.net/ef55d177-2075-4dc9-99bf-83549fdc8c62
Your API would now prompt for AAD Authentication both from browser and when accessed via code.





THE VERY NICE SCRIPT THANK YOU FOR THE NICE BLOG
ReplyDeleteAzure Training in Chennai | Certification | Azure Online Training Course | Azure Training in Bangalore | Certification | Azure Online Training Course | Azure Training in Hyderabad | Certification | Azure Online Training Course | Azure Training in Pune | Certification | Azure Online Training Course | Azure Training | microsoft azure certification | Azure Online Training Course
thanks for sharing....................!
ReplyDeleteRPA online training
RPA training
Ruby on rails online training
Ruby on rails training
Abinitio online training
Abinitio training
Android online training
Android training
Ansible online training
Ansible training
Appium online training
Appium training
AWS online training
AWS training
Azure DevOps online training
Azure DevOps training
Azure online training
Azure training
sccm training
ReplyDeletewindows admin training
mysql training
azure training
web methods training